MariaDB is an
relational
database management system (RDBMS). Generally we use single node
of database server for small application but think about application which have
thousands of users keep online at a time, In that
situation we need a structure which will capable to
handle this load and provides high availability. So we need to add
multiple database servers
interconnected with each other and keep synchronized, so in case any server
goes down other servers can take place of them and provide services to users.
MariaDB Galera Cluster is an synchronous Active-Active
multi-master cluster of MariaDB databases. Which keeps all nodes synchronized.
MariaDB Galera cluster provides synchronus replication which is always highly
available (there is no data loss when one of the nodes crashes, and data
replicas are always consistent). Currently it only
supports XtraDB/InnoDB storage
engines and available for Linux platform only.
This article will help you to setup MariaDB Galera
Cluster with 3 servers
running with CentOS. Cluster server details are as
following.
- Cluster DB1: 192.168.1.10
( HostName: db1 )
- Cluster DB2: 192.168.1.20
( HostName: db2 )
- Cluster DB3: 192.168.1.30
( HostName: db3 )
Note: Step
1/2/3 has to be done on all cluster nodes
and remaining steps are node specific.
Step 1: Add MariaDB Repositories
Create a mariadb repository
/etc/yum.repos.d/mariadb.repo
using following content in your system. Below repository will work on CentOS
6.x systems, For other system use
repository
generation tool and add to your system.
For CentOS 6 – 64bit
[mariadb]
name = MariaDB
baseurl = http://yum.mariadb.org/5.5/centos6-amd64
gpgkey=https://yum.mariadb.org/RPM-GPG-KEY-MariaDB
gpgcheck=1
For CentOS 6 – 32bit
[mariadb]
name = MariaDB
baseurl = http://yum.mariadb.org/5.5/centos6-x86
gpgkey=https://yum.mariadb.org/RPM-GPG-KEY-MariaDB
gpgcheck=1
Step 2: Install MariaDB and Galera
Before installing MariaDB Galera cluster packages, remove any existing MySQL
or MariaDB packages installed on system. After that use following command to
install on all nodes.
# yum install MariaDB-Galera-server MariaDB-client galera
Step 3: Initial MariaDB Configuration
After successfully installing packages in above steps do the some initial
MariaDB configurations. Use following command and follow the instructions on
all nodes of cluster. If will prompt to set root account password also.
# mysql_secure_installation
# service mysql start
After that create a user in MariaDB on all nodes, which can access database
from your network in cluster.
# mysql -u root -p
MariaDB [(none)]> GRANT ALL PRIVILEGES ON *.* TO 'root'@'%' IDENTIFIED BY 'password' WITH GRANT OPTION;
MariaDB [(none)]> FLUSH PRIVILEGES;
MariaDB [(none)]> exit
and stop MariaDB service before starting cluster configuration
# service mysql stop
Step 4: Setup Cluster Configuration on DB1
Lets start setup MariaDB Galera cluster from DB1 server. Edit MariaDB server
configuration file and add following values under
[mariadb]
section.
[root@db1 ~]# vim /etc/my.cnf.d/server.cnf
query_cache_size=0
binlog_format=ROW
default_storage_engine=innodb
innodb_autoinc_lock_mode=2
wsrep_provider=/usr/lib/galera/libgalera_smm.so
wsrep_cluster_address=gcomm://192.168.1.20,192.168.1.30
wsrep_cluster_name='cluster1'
wsrep_node_address='192.168.1.10'
wsrep_node_name='db1'
wsrep_sst_method=rsync
wsrep_sst_auth=root:password
Start cluster using following
command.
[root@db1 ~]# /etc/init.d/mysql bootstrap
Bootstrapping the clusterStarting MySQL.... SUCCESS!
If you get any problem during startup check MariaDB error log file
/var/lib/mysql/<hostname>.err
Step 5: Add DB2 in MariaDB Cluster
After successfully starting cluster on DB1. Start configuration on DB2. Edit
MariaDB server configuration file and add following values under
[mariadb]
section. All the settings are similar to DB1 except wsrep_node_address,
wsrep_cluster_address and wsrep_node_name.
[root@db2 ~]# vim /etc/my.cnf.d/server.cnf
query_cache_size=0
binlog_format=ROW
default_storage_engine=innodb
innodb_autoinc_lock_mode=2
wsrep_provider=/usr/lib/galera/libgalera_smm.so
wsrep_cluster_address=gcomm://192.168.1.10,192.168.1.30
wsrep_cluster_name='cluster1'
wsrep_node_address='192.168.1.20'
wsrep_node_name='db2'
wsrep_sst_method=rsync
wsrep_sst_auth=root:password
Start cluster using following
command.
[root@db2 ~]# /etc/init.d/mysql start
Starting MySQL..... SUCCESS!
Step 6: Add DB3 in MariaDB Cluster
This server is optional, If you want only two server in cluster, you can
ignore this step, but you need to remove third server ip from DB1/DB2
configuration files. To add this server make changes same as DB2.
[root@db3 ~]# vim /etc/my.cnf.d/server.cnf
query_cache_size=0
binlog_format=ROW
default_storage_engine=innodb
innodb_autoinc_lock_mode=2
wsrep_provider=/usr/lib/galera/libgalera_smm.so
wsrep_cluster_address=gcomm://192.168.1.10,192.168.1.20
wsrep_cluster_name='cluster1'
wsrep_node_address='192.168.1.30'
wsrep_node_name='db2'
wsrep_sst_method=rsync
wsrep_sst_auth=root:password
Start cluster using following
command.
[root@db3 ~]# /etc/init.d/mysql start
Starting MySQL..... SUCCESS!
Step 7: Test MariaDB Galera Cluster Setup
At this stage your cluster setup has been completed and running properly.
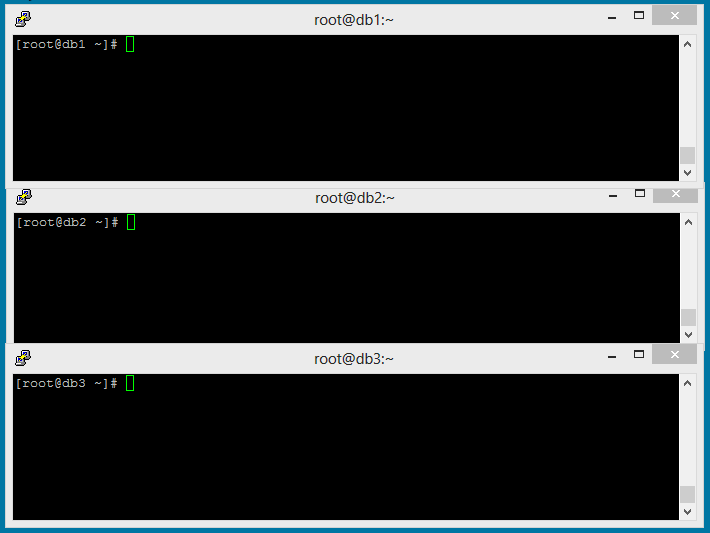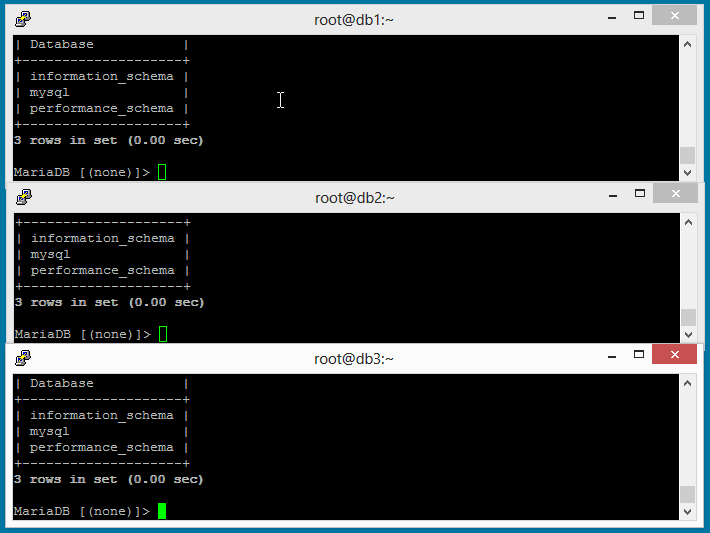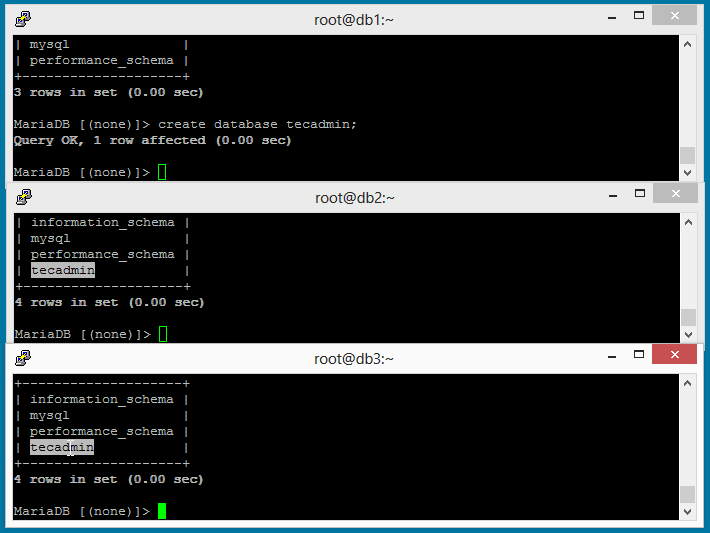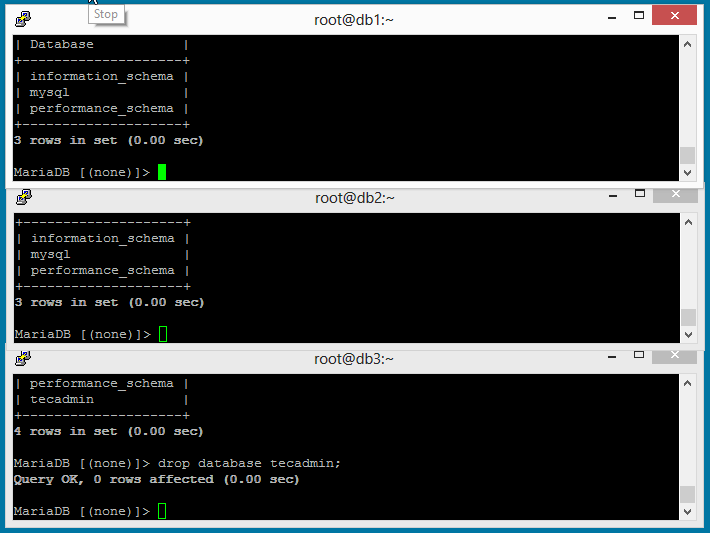
Now you can test the cluster setup by creating database and tables at any
server in cluster, it will replicate immediately to
all servers in cluster.
Above GIF image is showing that databases are replicating
properly to all nodes of cluster.
(tecadmin)