[X] what this text DOES NOT cover
[X] What is session hijacking?
[X] A little bit on cookies
[X] what this text DOES NOT cover
i will not cover arp poisoning!!!! this is strictly HTTP session session hjacking.
[X] what is session hijacking?
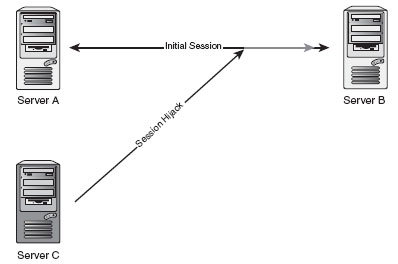
session hijacking is taking over a user session. essentially it is
when two computers establish a connection and an attacker
assumes the position of one of the computers through their
session id.
let's say...
1. an admin logs into his control panel of his website.
2. a session id is generated.
3. his computer mysteriously goes offline without logging out (hehe)
4. you can then guess his session id
5. if the session id is right, you can assume his admin privileges.
http sessions are stateless. i guess when they developed http
they weren't thinking about individual sessions. session id's
were ceated to track a single user for each page he viewed
without re-authenticating every time. a session id properly
identify's the user and allows them access.
session hijacking does require cookie theft, if you dont want
to guess the damn session id for years :P this is where xss
and other forms of exploits on web applications come in. if you
fail to see the "phpsessid=3209U3R6IMH2' in your browser then
most likely their is a hidden foreent on the
pae wth the phpsessid value. naturally this would be yours
if your logged in.
[X] little bit on cookies.
there are different types of cookies. the ones you need to know about
are persistent, non-persisent, and regular session cookies.
persistent cookies are cookies that stay active after the user closes
his/her webbrowser. if you check the 'remember me' button, this
will turn cookies into persistent cookies.
non-persistent cookies are cookies that close the session when
the user closes thebre, these are also called 'session cookies'.
[X] jacking the session.
ok, this one isnt hard. this is known as cookie theft, or in my old crew
a 'hot link'. example:
1. user A and user B are both logged in at mysite.com
2. user has no admin permissions. User B does.
3. user A messages, or posts a link somewhere for user B to click.
4. when user B clicks the link the 'hot link' logs their referrer.
so you would setup a php page to log referrers that visited
that page. something like
log.php
Code:
session_start();
if($_SESSION["logged"] != "yes")
{
* $agent = $_SERVER['HTTP_USER_AGENT'];
* $uri = $_SERVER['REQUEST_URI'];
* $ip = $_SERVER['REMOTE_ADDR'];
* $ref = $_SERVER['HTTP_REFERER'];
* $visitTime = date("r");*** *** //Example: Thu, 21 Dec 2000 16:01:07 +0200
*
*
* $logLine = "$visitTime - IP: $ip || User Agent: $agent* || Page: $uri || Referrer: $ref\n";
* $fp = fopen("visitorLog.txt", "a");
* fputs($fp, $entry_line);
* fclose($fp);
* $_SESSION["logged"] = "yes";
}
note: this does not work all the time. do not expect this to be the
only thing to hijack sessions with.
session hijacking is more in depth, but im at work and its not
a book, this si a simple way to hijack session ID's and assume the
identity of someone elses session. you can see your cookies in the
proper folder. check your browser's settings and FAQ before asking
where your cookies are located. you can also do a search on your
own computer to get a look at cookies.
wikipedia provides us with an example link of how to use javascript and a cgi file to capture cookies.
Code:
Click here!
a simple way to explain the link. the above link is a cgi script that will retreive the values of the previous pages cookies, then the cgi script would normally store them for later to browse through.
[X] What is session hijacking?
[X] A little bit on cookies
[X] what this text DOES NOT cover
i will not cover arp poisoning!!!! this is strictly HTTP session session hjacking.
[X] what is session hijacking?
session hijacking is taking over a user session. essentially it is
when two computers establish a connection and an attacker
assumes the position of one of the computers through their
session id.
let's say...
1. an admin logs into his control panel of his website.
2. a session id is generated.
3. his computer mysteriously goes offline without logging out (hehe)
4. you can then guess his session id
5. if the session id is right, you can assume his admin privileges.
http sessions are stateless. i guess when they developed http
they weren't thinking about individual sessions. session id's
were ceated to track a single user for each page he viewed
without re-authenticating every time. a session id properly
identify's the user and allows them access.
session hijacking does require cookie theft, if you dont want
to guess the damn session id for years :P this is where xss
and other forms of exploits on web applications come in. if you
fail to see the "phpsessid=3209U3R6IMH2' in your browser then
most likely their is a hidden foreent on the
pae wth the phpsessid value. naturally this would be yours
if your logged in.
[X] little bit on cookies.
there are different types of cookies. the ones you need to know about
are persistent, non-persisent, and regular session cookies.
persistent cookies are cookies that stay active after the user closes
his/her webbrowser. if you check the 'remember me' button, this
will turn cookies into persistent cookies.
non-persistent cookies are cookies that close the session when
the user closes thebre, these are also called 'session cookies'.
[X] jacking the session.
ok, this one isnt hard. this is known as cookie theft, or in my old crew
a 'hot link'. example:
1. user A and user B are both logged in at mysite.com
2. user has no admin permissions. User B does.
3. user A messages, or posts a link somewhere for user B to click.
4. when user B clicks the link the 'hot link' logs their referrer.
so you would setup a php page to log referrers that visited
that page. something like
log.php
Code:
session_start();
if($_SESSION["logged"] != "yes")
{
* $agent = $_SERVER['HTTP_USER_AGENT'];
* $uri = $_SERVER['REQUEST_URI'];
* $ip = $_SERVER['REMOTE_ADDR'];
* $ref = $_SERVER['HTTP_REFERER'];
* $visitTime = date("r");*** *** //Example: Thu, 21 Dec 2000 16:01:07 +0200
*
*
* $logLine = "$visitTime - IP: $ip || User Agent: $agent* || Page: $uri || Referrer: $ref\n";
* $fp = fopen("visitorLog.txt", "a");
* fputs($fp, $entry_line);
* fclose($fp);
* $_SESSION["logged"] = "yes";
}
note: this does not work all the time. do not expect this to be the
only thing to hijack sessions with.
session hijacking is more in depth, but im at work and its not
a book, this si a simple way to hijack session ID's and assume the
identity of someone elses session. you can see your cookies in the
proper folder. check your browser's settings and FAQ before asking
where your cookies are located. you can also do a search on your
own computer to get a look at cookies.
wikipedia provides us with an example link of how to use javascript and a cgi file to capture cookies.
Code:
Click here!
a simple way to explain the link. the above link is a cgi script that will retreive the values of the previous pages cookies, then the cgi script would normally store them for later to browse through.
No comments:
Post a Comment